Beware of targeted phishing attacks on UAA email
by Michelle Saport |
Over the past month, UAA has witnessed a significant increase in phishing emails to UAA employees that are made to look like they were sent by their supervisor or other university leadership. The emails start off with a simple question of "Are you available?" If the victim of the phishing responds, the attacker creates a sense of urgency by saying that they are in a meeting and can't talk right now, but that they need help with something important right away. At that point, the attacker asks them to purchase a gift card for them, usually for Amazon or iTunes.
In this recent string of phishing attacks, the attacker registered a gmail.com address that was made to look like it was coming from university staff as much as possible. In Gmail, you can see the sender's address at the top of the message, next to their name:
In this example, you can clearly see that the email did not come from an alaska.edu address.
Phishing emails will often urge you to act quickly because your account has been compromised, your order cannot be fulfilled, or another urgent matter. Be on the lookout for language mistakes (although there are fewer and fewer these days), suspicious URLs (web addresses), vague language, or .com or .org vs. .edu. in the web and email addresses.How do you avoid being a victim?
- Don't reveal personal or financial information in an email and do not respond to email solicitations for this information. This includes following links sent in email.
- Before sending sensitive information over the Internet, check the security of the website.
- Pay attention to the website's URL. Malicious websites may look identical to a legitimate site, but the URL may use a variation in spelling or a different domain (e.g., .com versus .net).
- If you are unsure whether an email request is legitimate, try to verify it by contacting the company directly. Contact the company using information provided on an account statement, not information provided in an email.
- Keep a clean machine. Having the latest operating system, software, web browsers, anti-virus protection and apps are the best defenses against viruses, malware, and other online threats.
What should you do if you believe you're a victim?
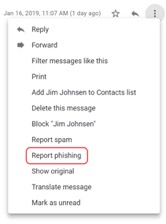
- Report the email as phishing to Google. Next to the reply button on the far right side of the message, there is a drop-down menu where you can select "Report Phishing." This alerts Google that the email is dangerous, and helps Google keep it out of other's inboxes.
- If you responded to a phishing email, report it to the Technical Support Center immediately. Don't wait. If the link compromised your computer, time could be very important. The Technical Support Center can also be on alert for any suspicious or unusual activity.
- If you believe your financial accounts may be compromised, contact your financial institution immediately and close the account(s).
- Watch for any unauthorized charges to your account.
Remember: UAA IT Services will never ask via email for any personal information. No reputable organization will either. Please be skeptical of any email you receive that asks you for personal or financial information.
 "Beware of targeted phishing attacks on UAA email" is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License.
"Beware of targeted phishing attacks on UAA email" is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License.